As the Industrial IoT (IIoT) continues to expand, more and more devices are being connected to networks. While this trend is enhancing operational efficiency, it is unfortunately causing asset owners to become increasingly concerned about the dangers posed by cybersecurity threats. The World Economic Forum Industrial Internet Survey noted that 64% of respondents stated that security concerns were one of the top four main barriers for businesses not embracing the IIoT trend. The asset owners’ concerns are justified.
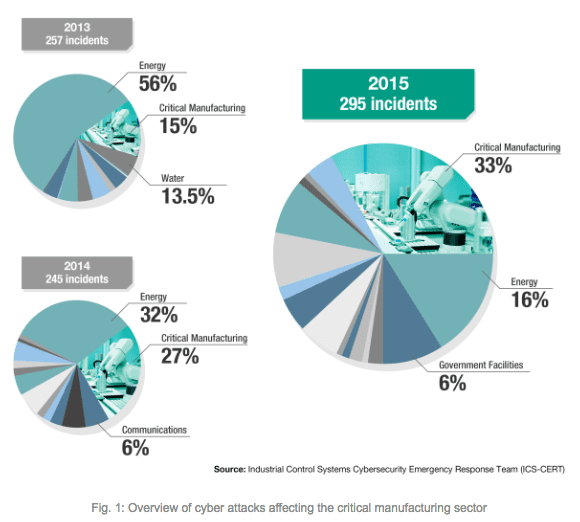
A recent report released by the Industrial Control Systems Cybersecurity Emergency Response Team (ICS-CERT) calculated that investigators responded to 295 incidents in 2015 in the U.S., compared to 245 the previous year, regarding cyber attacks on infrastructure.
It is even more concerning for the critical manufacturing sector, which saw the largest increase proportionally from 27% of the overall total in 2014 to 33% in 2015. It is therefore unsurprising that asset owners are increasingly requiring cybersecurity solutions to allow them to build secure systems for industrial applications.
How Cybersecurity Standards Began
In 2002, the International Society for Automation (ISA) produced the ISA-99 document to advise businesses operating in automation industries how to protect against cybersecurity threats. Fifteen years ago, cybersecurity wasn’t the hot topic it is today. The ISA documents have been aligned with those more frequently used by the International Electrotechnical Commission (IEC) as the concerns around cybersecurity have grown since the conception of the ISA standards. Currently, the IEC 62443 standard constitutes a series of standards, reports, and other relevant documentation that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS). If the guidelines within the IEC 62443 standard are followed, it significantly reduces the chances of a cyber attack affecting the network.
A Quick Glance at the IEC 62443 Standard
The IEC 62443 standard includes guidelines for different parts of a network and those who perform different responsibilities on the network. In the past, asset owners relied on system integrators (SIs) such as Siemens, Honeywell, and ABB to provide the security solutions for the network. However, many SIs now demand that component suppliers comply with the subsection of the IEC 62443 standard that pertains to their devices. The graph below provides a brief overview including the scope and the significance of each part for those who must ensure the secure operation of a network.
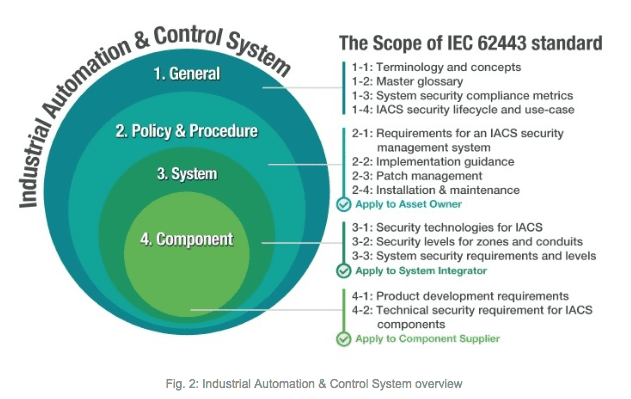
The IEC 62443 guidelines define four security threat levels. The security standard level 2 is the baseline requirement of the automation industry. It relates to cyber threats posed by hackers, which is the most common attack experienced by system integrators who secure industrial networks.
IEC 62443-4-2 Level 2: Baseline Requirements of the Automation Industry
Within the IEC 62443 standard are several subsections that relate to different parties. As SIs are demanding compliance with the IEC 62443-4-2 subsection, which issues guidelines for component suppliers, the subsection is becoming increasingly important. The component requirements are derived from foundational requirements, including account, identifier and authenticator management, password-based authentication, public key authentication, use control, data integrity and confidentiality, as well as backup for resource availability.
If component suppliers follow the set of guidelines that are set out under the IEC 62443-4-2 subsection, they will equip network operators with the best chance of being able to protect their networks against cyber attacks. Although the component suppliers must add certain features and capabilities to their devices in order for the devices to be suitable for deployment on Industrial IoT networks, the onus is really on the network operators to be able to utilize these features across their network and ensure that all of those who they grant access to the network are familiar with the best procedures contained within the IEC 62443-4-2 subsection.
Adherence to each of the guidelines under the IEC 62443-4-2 subsection will typically result in several positive outcomes that will go a long way to making the network more secure. However, not following the guidelines could have any number of negative consequences, all of which will result in the network being less secure and leave the network vulnerable to attack by those who have malicious intent.
Moxa’s Solutions
To enhance component-level cybersecurity, Moxa has introduced the latest switch firmware, called Turbo Pack 3, which supports additional security functions for switches, including enhanced MAC Address and RADIUS authentication. For more information download the white paper or give Colterlec a call on 1300 36 26 26.

