Introducing the New EDR-G9010 Series All-in-one Industrial Secure Router
Cybersecurity incidents are on the rise, and industrial control systems are being targeted more than before. In recent incidents where IT systems were compromised, we have noticed that asset owners had no choice but to shut down all systems to avoid further damage spread. With OT and IT converging, it becomes essential to build a robust first line of network defense to secure industrial control systems and infrastructure.
Moxa brings the answer with the EDR-G9010 Series of industry-certified all-in-one firewall/NAT/VPN/switch/routers featuring advanced security and high performance to safeguard your industrial applications.
Build Defense-in-depth Security for Your Industrial Networks
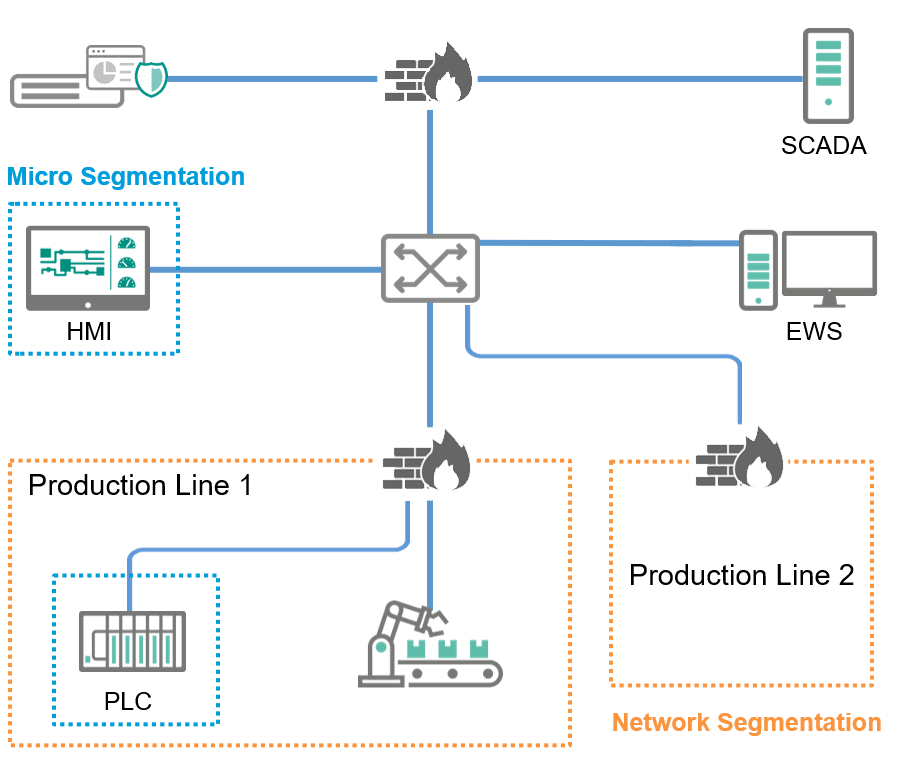
Network Segmentation
Flat network designs originally intended to ensure low-latency data communication and to maintain the availability of all systems are now a key security concern in OT networks. It is important to perform proper network segmentation to minimise risk without compromising performance.
Micro Segmentation
To protect critical assets, you need:
- Industrial Intrusion Prevention System (IPS)
- Virtual patch
- Hardware bypass
Network Segmentation
To build a security boundary, you need:
- High bandwidth
- Redundancy mechanisms
- Deep Packet Inspection (DPI) for industrial protocols
Secure Remote Access
Remote connections have become an essential part of industrial communications. However, despite the convenience of remote desktop protocols, connection security is often being overlooked.
It is important to build secure remote access channels to strengthen edge security while ensuring stable connection throughput.

Network Address Translation (NAT)
Consider IP addresses a gateway to your critical assets. To protect internal assets, all devices need a private IP address that communicates through a single public IP address. However, managing IP addresses can be a daunting task.
In addition, the public IP address is exposed to possible malicious actors. Therefore, it is imperative to have a mechanism to manage the IP addresses of your critical assets more efficiently.
High Security Meets High Throughput
EDR-G9010 Series 10-port Gigabit Industrial Secure Routers